Tonight was a Mad Maxathon (one, two and three).
Monthly Archives: February 2009
Movie night!
We watched Shaun of the Dead, Young Frankenstein, Clue, The Transporter and The Transporter 2. Excellent, classic, quality, exciting and enjoyable in that order.
Holiday!
No work for me today (or tomorrow, or Friday). Yay.
Bubbles on fire!
I sometimes have a candle on my desk or somewhere in the room, a scented one. At the moment it’s mulled wine. About 15 minutes ago Bubbles (cat #1) jumped up onto my desk, brushed passed the candle and set herself alight. She stepped over my keyboard and I managed to pat her on the side once pretty hard and the flames went out, but the damage was done. The room stinks of singed hair, Bubbles went sprinting out of the room not because of the flame, but because of me giving her a thump and then both myself and Grete making a lot of noise and ‘chasing’ type noises to check she was ok.
She was hiding upstairs, we dragged her out, brushed and combed her down, and she’s phsyically fine, although her pride is dented. She’s got a really thick multi-layer coat and the flames have singed the outer long hairs and the very tips of the second layer, but never got anywhere near her skin. We gave them both some tuna to help convince them they weren’t going to the vets (the normal result of ‘chase’ type noises).
Scary for a moment.
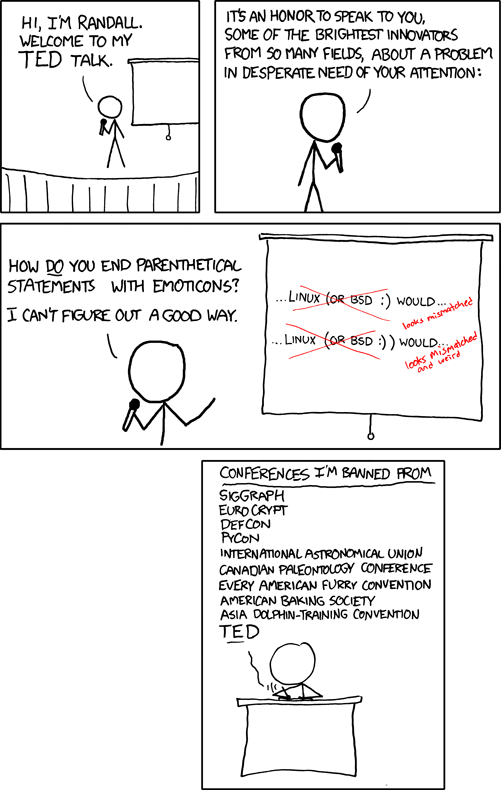
xkcd Strikes gold again
Cygwin and rsync and all things nice
I wrote a little while ago that I was running Linux (Ubuntu in this case) inside a VirtualBox virtual machine, and it was all good. Before that I’ve played with lots of methods of getting my favourite unix utilities (like rsync) working under Windows. I’ve used Cygwin, and pre-compiled Windows versions and stripped-down Cygwin versions, and second machines running Linux and VM’s.
One of the main drivers for getting those things working is to back up my websites, held on my hosting account. I can ssh into my hosting account, and that means if I can get rsync going locally, I can use it with ssh to copy all changes to my local machine. It’s efficient (rsync only copies changes) and it’s easy. The pain is always finding a decent compliant version of rsync.
Anyway, I already said that when I started using the Linux VM I ported my script across to that, and along with the VirtualBox shared folders, I could backup my websites and they were visible under XP. It wasn’t pretty but it worked, and it meant I had to start up the VM. At the start that wasn’t a problem because I was using it quite a bit but as the days went on and I stopped launching it, backups were less frequent.
And then today – random disaster. I crashed the VirtualBox VM image, and after a couple of restarts it eventually stopped booting. This wasn’t a great problem as I had snapshots of working images, so I just rolled back to one of those with two clicks. Two clicks which took less time than the following thought took to get from one end of my brain to the other ‘I made the snapshots weeks ago, and since then I’ve written a lot of scripts and downloaded a lot of files and you just erased them all you idiot’.
So, I set about repatching Ubuntu and setting up various settings that I’d lost and made a few more snapshots. But I needed a more permanent, reliable website backup solution.
Which means I’ve installed Cygwin again. I know there are Windows binaries for rsync, and I know there are other apps which claim to do the same thing, but you can’t (in my view) beat the simplicity of Cygwin and the unix binaries. Now I have a working cron daemon, ssh configured, rsync installed, and my little script which does all the work. The rsync command is pretty simple,
rsync –recursive –links –safe-links –rsh=ssh –stats –human-readable me@mywebhost:/myhomedir/ /path/to/local/copy/
Then I just tar up the resulting files, compress them, make sure the filename has a date in it, and I can be confident I’ve got copies of everything I need. Since most of my sites rely on mysql for their data, I also run some jobs on my webhost to mysqldump all the data into files three times a week, and I then back those files up locally. I could mysqldump the content remotely, but it’s a hell of a lot quicker to do it on their system, compress them, and then rsync the compressed files.
Installing ssmtp lets me send mail from the Cygwin command line, so the script can send me a mail when it’s finished, and I’ll schedule it in cron to run once a week or something. Much better.
Plus, I get all the fun of vi, grep and awk 🙂
Picking passwords
Found another article over at Dark Reading which explains why ‘clever’ passwords aren’t always clever. Worth a read.
The phpbb website was hacked
The guys who write the phpBB forum software have had their main website hacked. The whole process looked pretty sophisticated and the hacker had access for a couple of weeks (increasingly deep access during that time). The bottom line is that they have posted all the e-mail addresses, user ID’s and hashed passwords for every account registered on phpbb.com.
In fact, they went one further and just dumped the entire mysql database, and made it available, so it’s got all the fields of information used to register accounts.
Now the passwords are md5 hashes, rather than plain text, however phpBB v2 used a straight md5 hash which is easy to brute force. phpBB v3 salts the hash first, and so is harder to brute force. If you created an account on phpBB while it was running v2 and then never logged in again after it upgraded to v3 then lots of people you don’t want having access are currently trying to brute force your password. If you had a simple password, they’ve already done it, and in fact, they broke about 18,000 passwords pretty quickly (all the obvious ones).
Robert Graham has done some basic analysis of the passwords over in this article. He’s also posted a link to the blogger site which details the hack, which is still there at the moment, although none of the links from that site to the resulting files he published work. The phpbb.com site is down for maintenance until they make sure it’s safe and that nothing else was changed.
The hack was carried out using a 0-day exploit of PHPlist, a mail manager application, and not directly related to the phpBB software itself. The hacker had access for a couple of weeks, and the patches to PHPlist were released after he gained access, so patching as soon as they could wouldn’t have helped the phpBB guys. What would have helped, was not upgrading to the latest version of PHPlist straight away – a possible good argument for running at least one level back from the latest level of any software (excluding security patches, of course). Those two requirements probably conflict too often for it to be perfect advice.
I had an account on phpbb.com so I spent a few hours last night checking what user credentials I’d used and making sure I wasn’t using the same combination anywhere else. I think I had a reaonably strong password, it’s never a word in the dictionary, it’s not even a word in the dictionary with some letters replaced by numbers, so it can only be brute forced by using random combinations of characters. However, computational power is cheap and getting cheaper, so any password that can be brute forced will eventually be brute forced. I’m not sure if I logged in to phpbb.com after they moved to v3, but I suspect I did so my password was probably salted as well. However, I didn’t take any chances and I changed my passwords on a bunch of services last night.
Does this hack teach us anything? No, not really, but it reminds us of some stuff we should have already known. Try not to use the same user id / password combination more than once, and certainly keep stuff you care about (like online banking credentials) totally different to stuff you don’t care about (like message boards you’re going to use once).
The article analysing the passwords reminds us that picking clever passwords is harder than you first think, because with millions of other computer users around the world doing the same thing, passwords can still be very common. Picking trustno1 (Mulder’s password from X-Files) won’t help you when your hackers are X-Files fans, and joshua isn’t as clever as you imagined when you find out half the hackers in the world watched WarGames as well. I’m not sure the list on this site is really the top 500 passwords, but it’s a good example of 500 pretty weak passwords, because if they’re that easy to think up, they’re already in a brute force dictionary somewhere.
If you can create your own md5 hashes (various methods depending on your OS) then you can do a simple check to see if the password might be weak. Search for it on google. For example, the md5 hash for password is 5f4dcc3b5aa765d61d8327deb882cf99, now check out google and see how many hits you get for it. If someone used password as their password on phpbb.com then the hackers knew it in about 2 seconds. And making the o’s into zeros won’t help you. You don’t even need to be a hacker to go from unsalted md5 hashes to passwords, there are several websites out there, easily found in google, where you put in md5 hashes and they tell you the string used to create that md5 hash.
Take care with your accounts and your passwords, keep them out of the dictionary.
Listless and Restless
I guess technically you can’t be both listless and restless, but that’s sure how I feel.
Back from roleplaying
-5 celsius in Mansfield and -3 celsius in Nottingham (western edge). Pretty damn cold. Mansfield still has a lot of snow on the ground and any ungritted roads are really dangerous – the road down to our friends’ isn’t owned by the council yet and was slick with compacted snow and ice.
Made it in one piece though.
Gonna be a cold night.